Topic 6: Personal security
Risk and Security Risk Management
Standard, which consists of the following:
- Understanding the Background Context
- Identifying Risk
- Analysing Risk
- Evaluating Risk
- Treating Risk
Each of these steps will be discussed. Risk itself is defined as:
The probability of something happening that will have an adverse impact upon people, plant, equipment, financials, property or the environment, and the severity of that impact (AS/NZA 4360 2004).
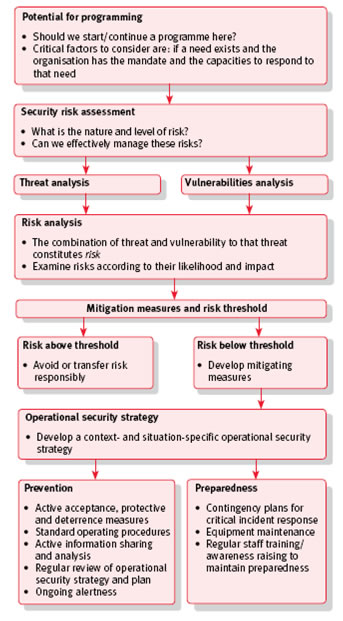
Security Risk Management basically follows a similar framework, and a diagrammatic representation is reproduced below.
Figure 6.1: Security Risk Management Framework Source: van Brabant, K., (2010). Operational Security Management in Violent Environments (Revised Edition), Good Practice Review, 8. London, UK: HPN, ODI. |
Understanding the Background Context
For risk management generally, as well as for security risk management specifically, it is vitally important to understand as much as possible about the background context relating to the project or program in question. The following two sections of van Brabant’s publication Operational Security Management in Violent Environments are particularly useful in relation to a security management situation:
- Context Analysis: Knowing where you are (section 2.3)
- Program Analysis: Know who you are, and what you want to do (section 2.4)
Risk Identification
Following efforts made at understanding the background context, it is important for involved stakeholders to then look at ways of identifying the risks which their communities may be facing. The traditional definition of risk uses a formulaic approach which sees risk as a function of hazards/threats, vulnerabilities & capacities (sometimes called resilience), expressed in the following relationship:
Risk (R) = Hazards (H) x Vulnerability (V)
Capacity (C)
In previous emergency management subjects (such as EMG308 Disaster Recovery, Sustainability and Resilience) you will have studied risk from the perspective of community vulnerability and resilience and the understanding that the human cost of disaster in terms of loss of livelihood, shelter and infrastructure, is a measure of a community’s vulnerability or resilience. For example an earthquake of magnitude 6.5 on the Richter scale occurring in a region with stringent building codes and a high degree of affluence may cause vastly less damage and consequent human suffering, than the same magnitude earthquake occurring in a region with little or no building codes and low resource capabilities. There is a tendency to compare these kinds of scenarios and pronounce the less affluent community “vulnerable”. This is true in terms of physical infrastructure and economic resources, but it may be that the poorer community actually has a great deal more social infrastructure.
Here in Topic 6 it is helpful to consider risk in the formulaic sense, i.e. as a combination of a hazard or threat, which is exacerbated by the degree of vulnerability which some of the community may exhibit. The capacity (in this formula sometimes called resilience) of the community is the degree to which they can draw on a number of their inherent strengths and resources to counter any perceived hazard or threat.
Emergency Managers in Australia use an All Hazards Approach, which means:
- assessing all potential hazards
- including all geographical areas
- involving all levels of government
- including all potential stakeholders
In practice there are three main ways to identify hazards or potential threats, and ideally these involve genuine interactive participation with the community at risk. It is also important to look at a combination of past, present and future hazards and to read and research them. The use maps or modern technology (e.g. satellite photography) also helps identify hazards or hazard trends
 |
|
Read through the following sections from van Brabant’s: Operational Security Management in Violent Environments:
Draw together points from both extracts into a one paragraph summary. |
|
Risk Analysis and Evaluation
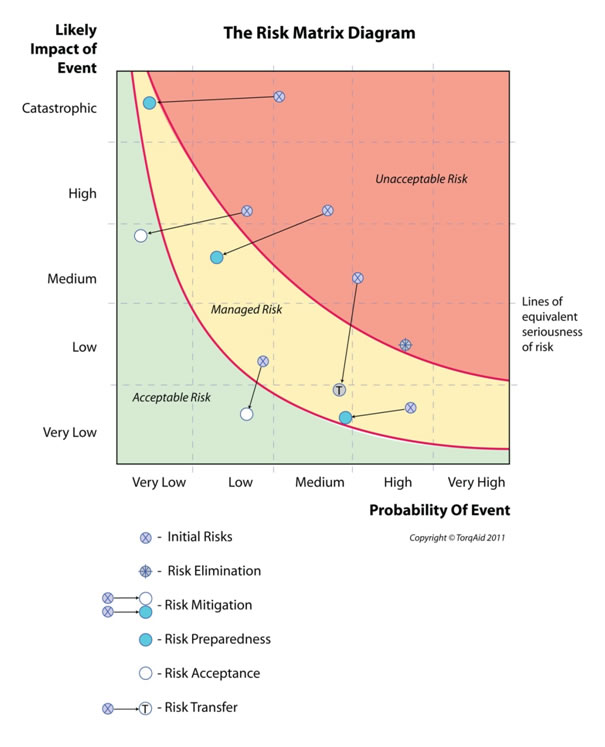
Once risks have been identified, they then need to be analysed. There are a number of methods to do this, the one we look at here is using a risk matrix which measures a combination of impact and likelihood.
Risks can then be evaluated (see Figures 6.2) by categorising them into three groupings:
- Unacceptable Risk
- Managed Risk
- Acceptable Risk
Risk Treatment/Reduction
Once risks have been evaluated, there are then traditionally five ways of treating or dealing with these. Ideally all the risks should end up in either the ‘Acceptable’ or ’Managed’ sectors of the Risk Matrix diagram. These five treatment methods are the following:
- Accepting the risk as it stands (see Figure 6.2 and the risks which reside in the ‘Risk Acceptance’ zone)
- Prevention or elimination of risk. Whilst this may be attempted, in practice this may be relatively rare
- Mitigation of risk. This means efforts designed to reduce either the impact and/or likelihood of the risk in question (see Figure 6.2, and the examples of risks being mitigated down towards the left-hand corner)
- Preparedness initiatives designed to deal with residual risk (these often complement risk mitigation initiatives)
- Transfer of risk (e.g. through insurance)
Risk Reduction is a term which combines the last four of these approaches, namely, Prevention/Elimination, Mitigation, Preparedness and Transfer. If, after risk reduction initiatives take place, there are one or more risks which remain in the ‘Unacceptable Risk’ zone, this has the potential to serious comprise the project or program.
 |
|
|
|
Risk Matrix diagram
- Compare Figure 6.2 and the three main zones (namely Unacceptable Risk; Managed Risk; and Acceptable Risk), with the diagram shown at Table 8 (p.49) of van Brabant’s Operational Security Management in Violent Environments.
- Read through the following sections from van Brabant’s Operational Security Management in Violent Environments. Basically these are two variants of the same overall model.
- Threat Assessment (Section 2.5)
- Vulnerability Assessment (Section 2.6)